What is Zero Trust Network Access (ZTNA) and what does it do? Read more in our Learning Center. What is ZTNA?
Cloudflare Access
Internet-native Zero Trust Network Access (ZTNA)
- Create an aggregation layer for secure access to all your self-hosted, SaaS, or non-web applications
- Connect users faster and more safely than a VPN
- Try it forever for up to 50 users with our Free plan
Strengthen the employee experience
Improve team productivity with modernized security that makes on-prem apps feel just like SaaS apps. No more slow, clunky VPNs or employee complaints.
Eliminate lateral movement
Reduce cyber risk and shrink your attack surface by granting context-based, least privilege access per resource rather than network-level access.
Scale Zero Trust effortlessly
Improve tech efficiency by protecting critical apps or highest risk user groups first, then expanding Internet-native ZTNA to protect your entire business.
Cloudflare is the only new vendor in the 2023 Gartner® Magic Quadrant™ for SSE
Cloudflare has been recognized in the 2023 Gartner® Magic Quadrant™ for Security Service Edge (SSE) report. We believe our recognition validates our commitment to continue advancing our Zero Trust platform to help secure hybrid work.
Cloudflare named a "Leader" in 2023 IDC MarketScape for Zero Trust Network Access (ZTNA)
IDC cites Cloudflare's "aggressive product strategy to support enterprise security needs." We believe our recognition validates our approach to help businesses of any size get started with Zero Trust and secure access for any user to any resource, without VPNs.
Cloudflare named a "Leader" in 2022 KuppingerCole Leadership Compass for ZTNA
Through its 2022 ZTNA market analysis, KuppingerCole Analysts AG cited several Cloudflare strengths such as our fully integrated organically developed security platform, large global cloud infrastructure, and massive market presence.
Top use cases for Access
- VPN replacement - Access is faster and safer than traditional VPNs. Start offloading critical apps for better security and end user experience.
- Accelerate mergers & acquisitions - Avoid a traditional network merge entirely. Integrate with multiple IdPs and provide per-app internal access during M&A.
- Contractor access - Authenticate third-party users like contractors with clientless options, social IdPs, and more.
- Developer access - Provide privileged technical users secure access to critical infrastructure without performance tradeoffs.
- Phishing-resistant MFA - Roll out strong authentication, like FIDO2-compliant security keys, everywhere.

Tackle Zero Trust one step at a time
Easy setup and management
Radically simplify the setup and operation of on-ramping traffic to private resources with app connector software and tunnel orchestration.
Seamless, always-on experience
Achieve peak end user performance and resilience to network outages with Cloudflare's global Anycast technology, ensuring reliability.
Rapid, early-adopter innovation
Keep up with the evolution of the Internet itself with a Zero Trust provider that constantly out-innovates its peers to make app access faster and more secure.
How it works
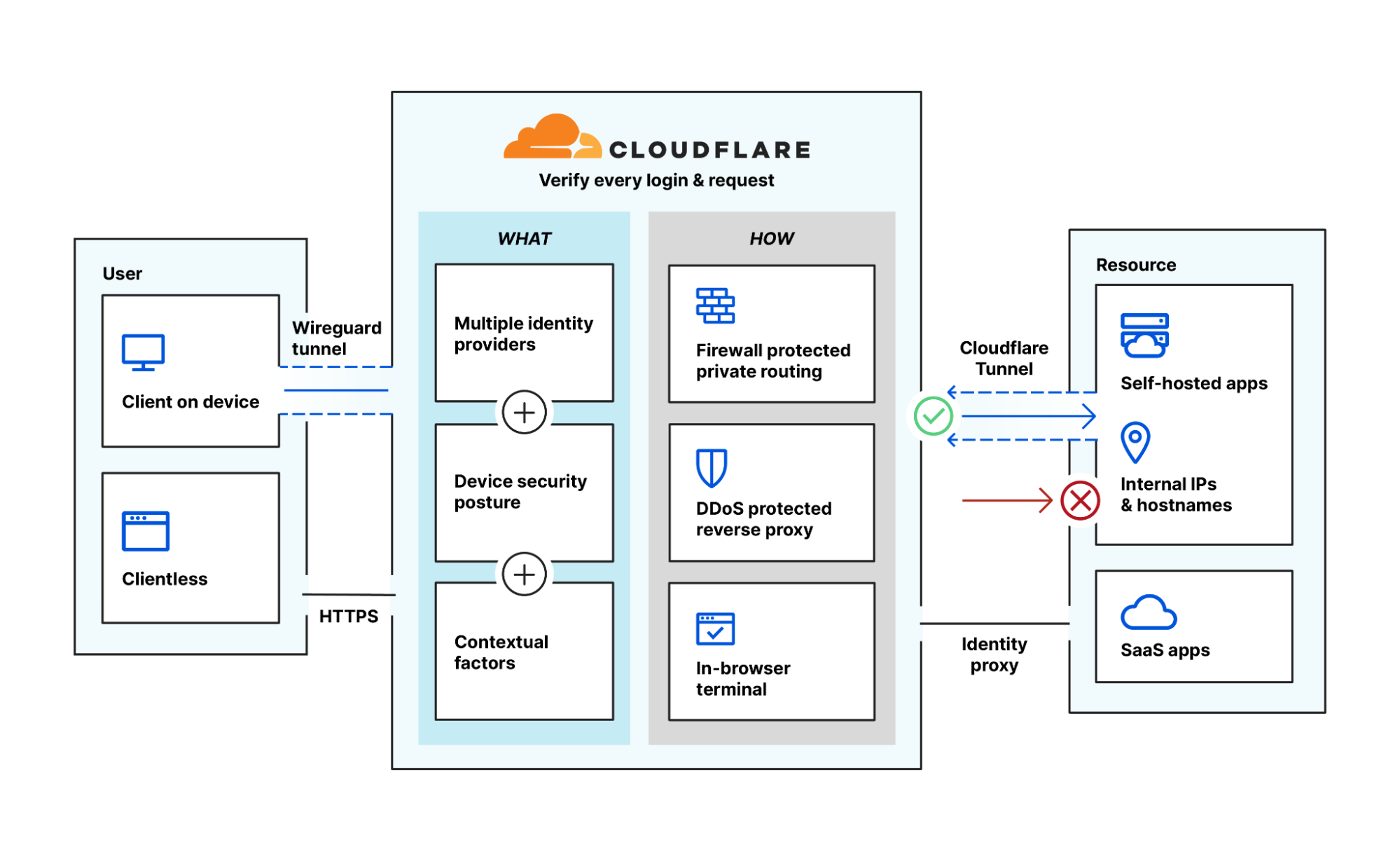
- Clientless capabilities support HTTPS traffic and in-browser SSH or VNC terminals, while our device client can help evaluate device posture or extend traffic to other in-line services like Cloudflare Gateway
- Access verifies identity and device posture and grants continuous, contexual access to all of an organization's internal resources, creating a software-defined perimeter
- In-line WAF and DDoS threat mitigation further strengthen L7 security for apps protected behind Access

Helping organizations worldwide progress towards Zero Trust
Tackle Zero Trust one step at a time
Additional resources

How to augment or replace your VPN with Cloudflare
See why and how to offload key applications from your traditional VPN to Cloudflare Access.

Zero Trust guide to securing contractor access
Read how ZTNA makes connecting third-party users like contractors and partners secure and simple.

Zero Trust guide to developer access
Unburden technical teams with safer, faster access to critical tools and infrastructure.

How strong authentication helps stop phishing attacks
Learn how ZTNA can help require strong authentication, like security keys, and roll it out everywhere.


