The ripple effect of compromised credentials

44% of employees use the same credentials for personal and work accounts, increasing risk to the enterprise


Risk grows as multi-vector becomes norm
Attackers targeting two (or more) vectors at a time - have dramatically improved their chances of successful entry

APIs: Business benefits & risks
92% of organizations faced an API attack in the last year — resulting in $12 billion in losses

Internet shutdowns in Iraq and Algeria
Nationwide Internet shutdowns intended to prevent cheating on academic exams results in millions of USD$ lost

The good, the bad, and the ugly
State of the Internet and the security challenges that businesses face today
Receive a monthly recap of the most popular Internet insights!
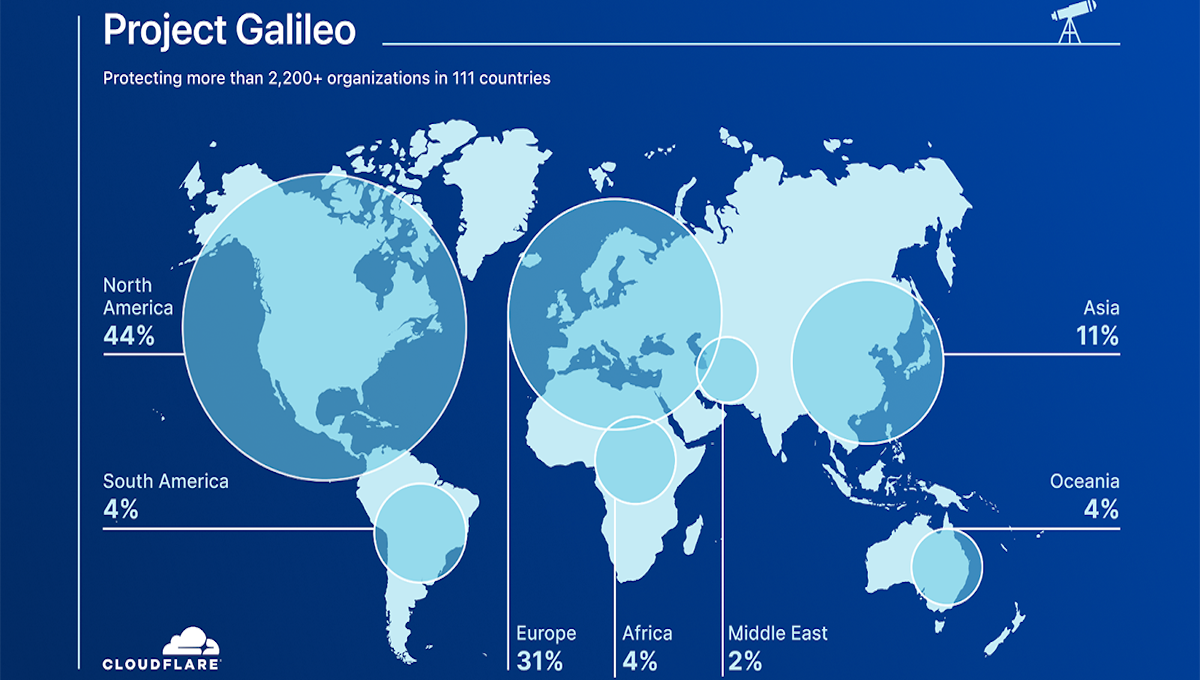
Protecting 2,200+ at-risk domains
Shedding light on the challenges at-risk public interest groups face from malicious actors looking to silence them

Internet disruptions in Pakistan
How the arrest of former Prime Minister; Imran Khan impacted the country & its Internet use

Overcoming down market constraints
Building easy-to-integrate & financially viable products for SMB can become an asset when selling to enterprise

The state of DDoS: New year, new threats
Large-scale volumetric attacks continue to grow as hacktivist target web hosting & cloud computing

Current state of application attacks
Profiling a year of attacks targeting the applications that run business

The CISO's guide to API security
Balancing API security without slowing down innovation

'23 Q1 DDoS threat report
DDoS grew 60% YoY with non-profit and broadcast media as prime targets

Current state of application attacks
Profiling a year of attacks targeting the applications that run business

Trends: Easter and Ramadan
In many countries, this holiday week saw the least Internet traffic of 2023

Q1 disruptions to the Internet
The impact of government-directed shutdowns, cyber attacks, and natural disasters

API growth parallels attacks
API attacks have reached an all-time high with 53% of data breaches attributed to compromised API tokens

Known hacktivists threaten more attacks
Killnet and AnonymousSudan credited for attacks against Western interests with threats to expand
Cyber attacks breach MFA
Attackers uncovering new ways to exploit even the most advanced security measures like MFA

Preying on Silicon Valley Bank
The FDIC is guaranteeing that SVB customers’ money is safe while bad actors are attempting to steal it

50 most impersonated brands
Okta, Microsoft, and Amazon are among the top brands used in phishing campaigns

Killnet cyber attacks on healthcare
As healthcare becomes more reliant on the Internet, the stakes for protecting patient data have increased

Attacks up 49% on Holocaust EDU
In honor of Remembrance Day, a deep dive into this and other nonprofits as the 6th most targeted industry

Securing Microsoft 365
70% of the enterprise uses M365 making it one of the largest attack surfaces

The anatomy of Vendor Email Compromise
Slow play attacks with bigger payouts are emerging as adversaries get more sophisticated
NCR: Securing online banking
Ensuring customer success means combatting fraud and attacks as more transactions move online

Attack surface grows with API proliferation
The rapid growth of APIs has led to significant security risks for the enterprise

The risks of security monitoring fatigue
4 recommendations to reduce data overload and burnout

Security for the holidays
Prepare for the attacks with the greatest risk to your organization

Ransomware attackers escalating extortion
7 trends raising the stakes and intensifying negotiations

BEC loss is rising
Highly targeted, difficult-to-detect phishing attacks are behind recent headlines

Bypassing MFA: The latest exploit
5 ways a Zero Trust strategy can help prevent MFA exploitation and protect user data

Using DDoS threats to extort organizations
Attackers proving willing to carry out ransom threats using network DDoS

Internal threats reach annual $600K cost
Remote work makes malicious insider attacks difficult to detect

The growing cost of shadow IT
80% of employees adopt unsanctioned SaaS applications -- exposing the corporate network

The risks smaller DDoS attacks pose
Attack techniques are evolving away from large-scale attacks to focus on smaller, shorter DDoS campaigns
